Practical Malware Analysis, Lab 11-1
This is a walkthrough of the Lab 11-1 from the book Practical Malware Analysis. The sample under analysis, Lab11-01.exe, is a credential stealer that performs GINA interception.
The samples for this lab can be downloaded from here.
Let’s start!
Static analysis
I’m going to perform some basic static analysis first.
Checking with PEiD I see that this sample is not packed - PE sections looks good too (no strange names, virtual and raw sizes are similar).
Hashes
Lab11-01.exe
| MD5 | a9c55bb87a7c5c3c923c4fa12940e719 |
| SHA1 | d971656c6c605a6e2130ab83a38420e655428f94 |
| SHA256 | 57d8d248a8741176348b5d12dcf29f34c8f48ede0ca13c30d12e5ba0384056d7 |
Interesting strings
GinaDLL
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
msgina32.dll
MSGina.dll
UN %s DM %s PW %s OLD %s
msutil32.sys
Looking at the strings I can guess that this malware performs GINA interception (GINA stands for Graphical Identification and Authentication). This is a technique used to steal users credentials: the malware adds its own DLL (probably msgina32.dll) into those loaded during the Windows logon process - such DLLs are listed (if any) in the registry key SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\GinaDLL and will be loaded at logon in addition to the original DLL MSGina.dll.
The string UN %s DM %s PW %s OLD %s looks like a formatted string so I expect that this malware will be printing something out.
The last one is the name of a file (msutil32.sys): don’t know what it is yet, but I will soon do.
Interesting imports
The malware imports:
- from
ADVAPI32.DLL,RegCreateKeyExandRegSetValueEx - from
KERNEL32.DLL,FindResource
So apparently it will create registry key/value, and this is coherent with what I was expecting from the strings analysis.
The FindResource is a hint that this malicious program may contain some embedded resource. Let’s look at the PE structure then.
PE structure
There is a .rsrc section that contains a resource named TGAD: this resource is an embedded executable as it contains the MZ signature and the !This program cannot be run in DOS mode. string. So the sample is probably a dropper. I can dump the embedded PE file for further analysis using the Resource Hacker tool.
Static analysis of the embedded PE file
Lab11-01-embedded.dll
This PE file is a DLL: the Characteristics header has the value IMAGE_FILE_DLL set.
It is not packed.
Hashes
| MD5 | 7ce4f799946f0fa44e5b2b5e6a702f27 |
| SHA1 | 951fb5b80702d02e5c327b56cc709ee3ad5523d2 |
| SHA256 | f8a4f61bccd5bab1cad0ab9e57f6f3092a8bd4dd0adfcd4853e89ba96afc93f9 |
Interesting strings
The strings from this PE file are included in those I already analyzed from the parent executable.
Interesting exports
The DLL exports many functions from the original msgina.dll: this is expected if this malware performs GINA interception.
A couple of interesting exports are WlxLoggedOnSAS and WlxLoggedOutSAS, since these functions are good points to perform malicious behavior.
Let’s continue analysis with IDA Pro now!
Advanced static analysis of the main executable with IDA Pro
At the beginning of the _main function (0x40120F) the malware calls sub_401080. This function extracts the resource named TGAD from the PE file.
Reading the code block between 0x40114A and 0x4011A2, the program writes the embedded resource to a file named msgina32.dll, which is placed in the same directory as the executable.
So I will rename this function to Sub_ExtractDll.
At 0x401288 the program calls the function sub_401000. This function creates the registry key SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon and then sets the value GinaDLL; the value is set with the fullpath and name of the dropped msgina32.dll.
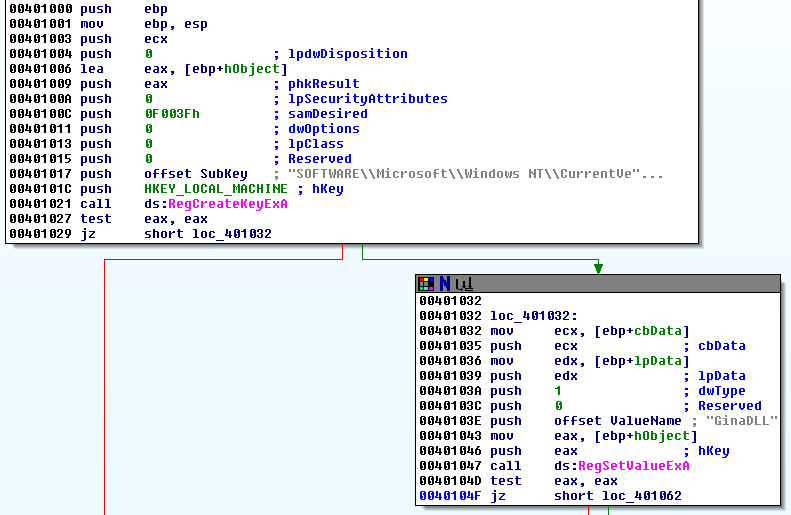
This way the malicious DLL will be loaded during the winlogon process (GINA interception).
I will rename this function to Sub_InstallGinaInterception.
Advanced static analysis of the dropped DLL with IDA Pro
The _DLLMain function loads the library MSGina.dll (at 0x100001099) from the Windows system directory (at 0x1000107E). The handle to the original msgina.dll is placed in a global variable named hModule (at 0x100010A1).
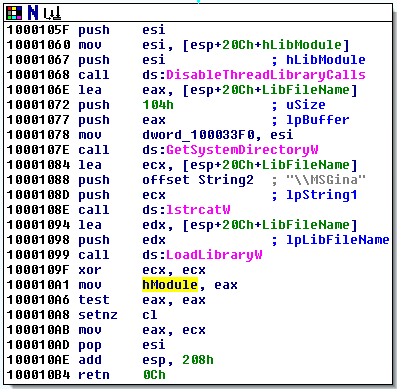
Most of the exported functions simply call the same function from the original msgina.dll.
For instance, this is the WlxLoggedOnSAS function:
10001350 push offset aWlxloggedonsas ; "WlxLoggedOnSAS"
10001355 call sub_10001000
1000135A jmp
The function sub_10001000 takes one parameter (the name of the function); its code gets the address of that function from the original msgina.dll module (the handle to such module is the global variable hModule set during _DLLMain); then it returns such address.
After the call, the malicious WlxLoggedOnSAS jumps to the address returned by sub_10001000, i.e. to the same WlxLoggedOnSAS function in the original DLL. It’s interesting to note that it performs a jump and not a call (so a new stack frame is not set).
The exported function WlxLoggedOutSAS has some extra behavior in addition to calling the original WlxLoggedOutSAS (at 0x100014E0).
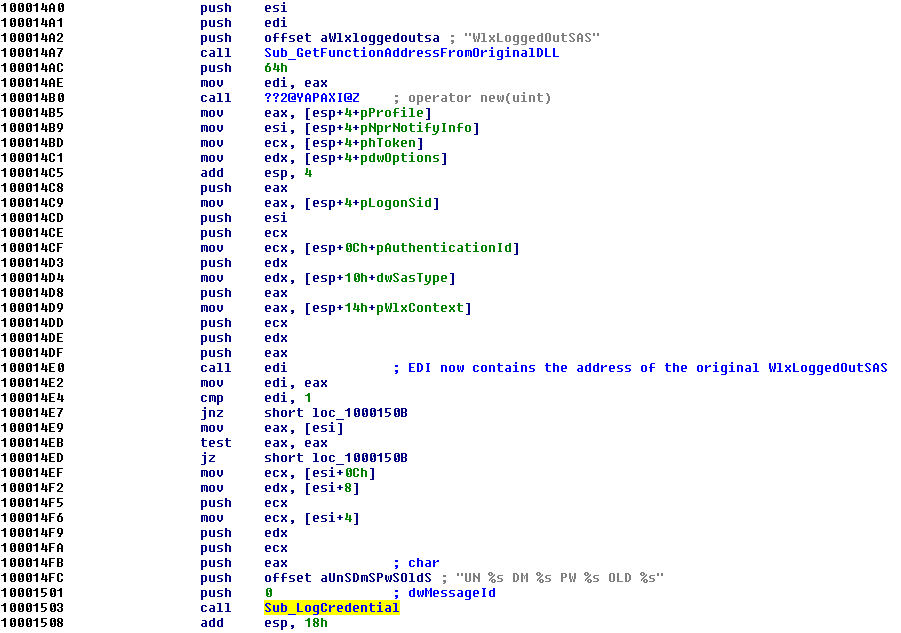
Note: How can I identify which is the modified function among all the exported functions? One option is just by guessing: functions
WlxLoggedOnSASandWlxLoggedOutSASare called when the user logs on and logs out, so they are good point to insert malicious code for stealing credentials. I can also try to search for the stringUN %s DM %s PW %s OLD %s.
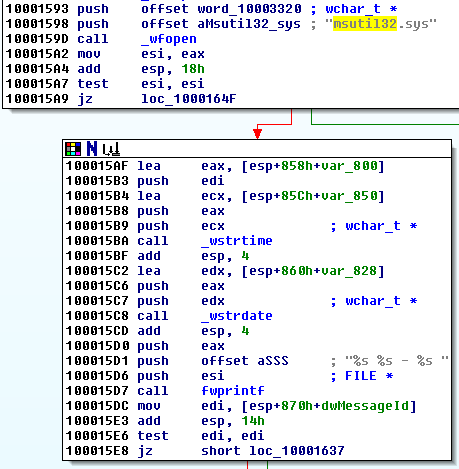
At offset 0x10001503 the DLL calls the function sub_10001570. This function writes stolen information (along with a timestamp) into a file named msutil32.sys (at 0x1000159D). So this file is actually a log file and not a driver as its extension was suggesting.
I will rename this function to Sub_LogCredential.
Dynamic analysis
After performing basic dynamic analysis (with the tools RegShot, Procmon, Process Explorer, Autoruns) and rebooting the system, I will log on, log out and then log on again. Here is the content of the file %SystemRoot%\System32\msutil32.sys:
02/14/19 21:23:08 - UN remuser DM REMWINDOWSXP PW password OLD (null)
Conclusions
So to wrap up and answer the questions:
1) What does the malware drop to disk?
The malware drops a DLL which is embedded in the PE resource section named TGAD.
2) How does the malware achieve persistence?
The malware installs msgina32.dll as a GINA DLL by adding it to the registry key SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\GinaDLL.
3) How does the malware steal user credentials?
The malware steals Windows user credentials by performing GINA interception during the logon process.
4) What does the malware do with stolen credentials?
The malware writes the stolen credential to the file %SystemRoot%\System32\msutil32.sys. The username, domain name, password and old password are logged, along with a timestamp.
5) How can you use this malware to get user credentials from your test environment?
After the malware installs itself the first time, a system reboot is required to make it active. Then the malware will log credentials when the user logs out.
That’s all for this lab!