Malware Lab Howto: Hardening VirtualBox and the Windows VM
This is a walkthrough on how to create and “harden” a Windows VM on Virtualbox so that it is not easily detected as a VM.
I’m going to use the antivmdetection script by nsmfoo.
At the end of the procedure, I will test the environment using Pafish, Al-Khaser and VMDE; these tools perform a series of checks employing several techniques to detect sandboxes and analysis environments in the same way as malware families do.
As we’ll see, not every check will pass. Obtaining a perfect environment (i.e. all checks passing) would require more complex hardening techniques including patching and re-compiling VirtualBox. This is out of the scope of this procedure - maybe in the future ;). The goal of this procedure is to obtain an environment good enough for manual analysis of malware and, at the same time, being fairly easy to do.
This was tested on an Ubuntu 18.04 host with VirtualBox 5.2.10, and using Windows 7 x64 Enterprise as the guest (a customized Windows installation package was used).
Preparatory steps
-
Get the antivmdetection script:
git clone https://github.com/nsmfoo/antivmdetection.git -
The script will require a few dependencies in order to perform the dumping of DSDT (see later):
sudo apt install acpidump libcdio-utils python-dmidecode -
Download VolumeID and DevManView and place the correct executables (x86 or x64) in the same folder as antivmdetection.
-
Perform the following (I used “cert” as the username and “lab” as the computer name):
cd antivmdetection
echo "some-username" > user.lst
echo "some-computername" > computer.lst
Creating the virtual machine
Create an empty virtual machine with these settings:
- CPU: 2 cores
- RAM: 4 GB
- HDD: 90 GB (dynamic)
- I/O APIC enabled
- Pointing Device: USB Tablet (default)
- Paravirtualization: None
- VT-x/AMD-V enabled (this is needed for x64)
- Nested Paging enabled
- GPU: 128 MB Video Memory and no acceleration set
- NIC: 1x Host-Only adapter
I named my virtual machine win7x64-kit-01.
Please note that having at least 2 cores, at least 2 GB of RAM and at least 80 GB of hard disk space, is critical because those are a few things that a malware will check to detect if it’s running in a lab environment.
Dumping the DSDT and generating the hardening scripts
The Differentiated System Description Table (DSDT) is part of the ACPI specification and contains information that may reveal that you’re running in a virtual machine. We can dump the DSDT off a physical system and use it to replace the one in the virtual machine.
Before turning on the VM for the first time, run antivmdetect.py as root:
sudo antivmdetect.py
The antivmdetect.py script will perform a few things:
- dump the DSDT table
- generate two scripts to be used later on
The script must be run on a physical system where the dumped DSDT results smaller than 64KB; if the DSDT is larger that 64KB VirtualBox will refuse to start the VM. I was successful at doing this on an old Asus Eee PC netbook (1015PEM model) and on an old HP desktop (HPCompaqPro6300SFF model), after booting with a Live Ubuntu distro.
What if you can’t find any suitable physical system to dump a smaller-than-64KB DSDT? You can try dumping the DSDT off a Windows system (either physical or virtual, as long as it’s the same version as the one we’re going to use for the lab), and then modifying it. [ TODO INSTRUCTIONS ]
In my case the generated files are:
DSDT_HPCompaqPro6300SFF.bin
HPCompaqPro6300SFF.ps1
HPCompaqPro6300SFF.sh
The binary file is the dumped DSDT. The bash script must be run before installing Windows, and the Powershell script must be run inside the Windows guest after Windows installation.
Before moving on, verify that the bash script contains a correct path to the DSDT binary:
VBoxManage setextradata "$1" "VBoxInternal/Devices/acpi/0/Config/CustomTable" /home/cert/tools/antivmdetection/DSDT_HPCompaqPro6300SFF.bin
I also manually reviewed the generated bash script a little bit so that the extradata values are all set (i.e. no commented rows, no empty values); I also removed those string: stuff from a couple of values.
Hardening: round one
Make sure that VirtualBox is not running (just close any VirtualBox window).
Run the bash script, providing the VM name as a command line argument:
./HPCompaqPro6300SFF.sh win7x64-kit-01
Installing Windows
Open VirtualBox, mount the Windows ISO on the VM and install Windows.
(This is probably just for me, due to my custom Windows installation kit) My Windows installation complains that the processor model is not supported (that’s weird) thus it won’t be able to install security updates. Maybe it depends on how the Windows installation kit was prepared, anyway I’m going to ignore this for now (not really interested in security updates).
Take a snapshot of the VM.
Post-installation
Perform the following:
- Tweak system performance settings
- Disable the automatic reboot on system crash
- Disable System Restore (and remove any restore points)
- Disable UAC
- Disable Windows Defender
- Disable Windows Firewall (but leave the Service on)
- Disable Windows Update
- Set the execution policy of PowerShell scripts (from a PowerShell prompt:
Set-ExecutionPolicy Unrestricted)
(This is probably just for me, due to my custom Windows installation kit) Notice that a VMware driver was left in the Windows installation kit: uninstall the
VMware pointing deviceremoving the driver and make sure the driver gets removed from the filesystem (if needed, delete it manually:del C:\WINDOWS\system32\drivers\vmmouse.sys); reboot the system.
Take a snapshot of the VM.
Hardening: round two
Move the antivmdetection folder to the Windows guest. A quick way is to make an ISO of the folder on the Linux host and mount it in the Windows VM.
genisoimage -U -o tools.iso tools
Copy the antivmdetection folder somewhere in Windows, then run the PowerShell script HPCompaqPro6300SFF.ps1.
It will ask to disable the “confirm on delete” from the Recycle Bin properties.
When done, it will reboot the system.
Run it again after reboot to let it finish.
Take a snapshot of the VM.
Hardening: round three (aka Rehardening)
A few things still need to be set and they need to be set after each Windows reboot:
- Rename the registry keys under
HKLM:\HARDWARE\ACPI\DSDTto remove any reference to VirtualBox - Rename the registry keys under
HKLM:\HARDWARE\ACPI\FADTto remove any reference to VirtualBox - Modify the value of
SystemBiosDateand theVideoBiosVersionunder the registry keyHKLM:\HARDWARE\DESCRIPTION\SYSTEM - Uninstall the “Base System Device” hardware (this avoids failure of the WMI check)
I made a PowerShell script (rehardening.ps1) that automate these steps. It needs DevManView to uninstall the hardware; the syntax is DevManView.exe /uninstall <Device Instance ID> (read the Device Instance ID using DevManView).
To execute it at boot, create a Scheduled Task that calls a .bat file which in turn runs PowerShell.
This is the content of my .bat file:
@echo off
cd C:\tools\antivmdetection\extra
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -command ./rehardening.ps1"
We’re done! Don’t forget to take a snapshot of the VM!
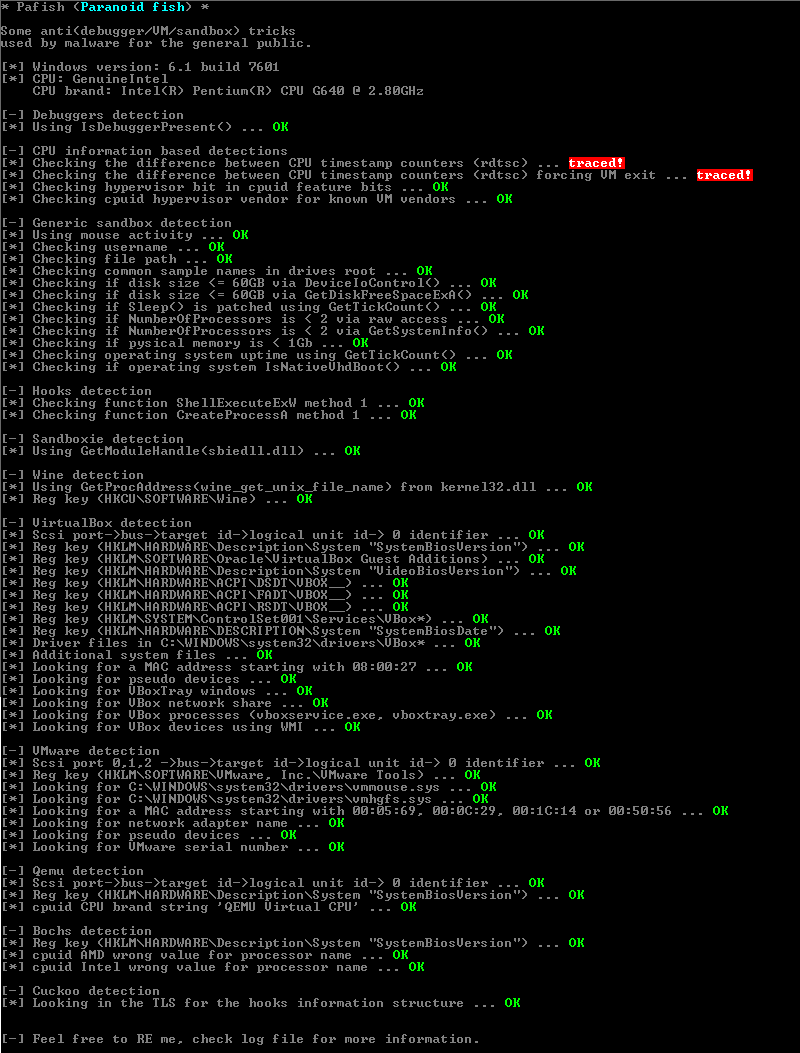
Pafish
Time to check if hardening actually works as expected!
Run pafish, result should be as in the image:
Al-Khaser
[ TODO ]
VMDE
[ TODO ]
That’s all!