Practical Malware Analysis, Lab 1-2
This is a walkthrough of the Lab 1-2 from the book Practical Malware Analysis. The sample under analysis, Lab01-02.exe, has been packed so we will need to unpack it before performing static analysis.
Please note that there may be many different (and even better) ways to solve this lab, so the one described here is just my solution.
The samples for this lab can be downloaded from here.
Let’s start!
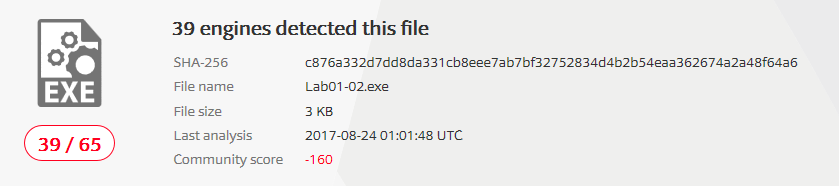
1) Upload the Lab01-02.exe file to VirusTotal. Does it match any existing antivirus definitions?
I will compute the hash first and then look for that hash on VirusTotal.
| MD5 | 8363436878404da0ae3e46991e355b83 |
| SHA1 | 5a016facbcb77e2009a01ea5c67b39af209c3fcb |
| SHA256 | c876a332d7dd8da331cb8eee7ab7bf32752834d4b2b54eaa362674a2a48f64a6 |
The VirusTotal report is available at the following links:
At present date the file is identified as malicious:
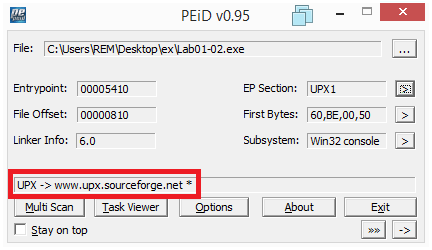
2) Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
We can analyze the file with PEiD and see that it’s been packed with UPX.
Looking at the PE sections also reveals signs of packing:
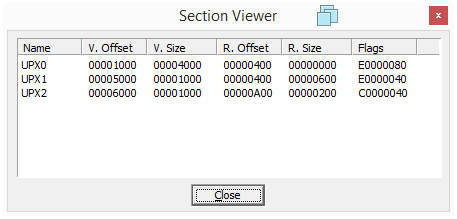
| Section | Virtual Size | Raw Size |
|---|---|---|
| UPX0 | 4000 | 0 |
| UPX1 | 1000 | 600 |
| UPX2 | 1000 | 200 |
Sections sizes in memory and on disk have suspicious values, for instance the UPX0 section has a size of 0 bytes on disk but its size in memory is 0x4000 bytes: this is a strong indication of packing. Sections names indicate that the UPX packer was probably used.
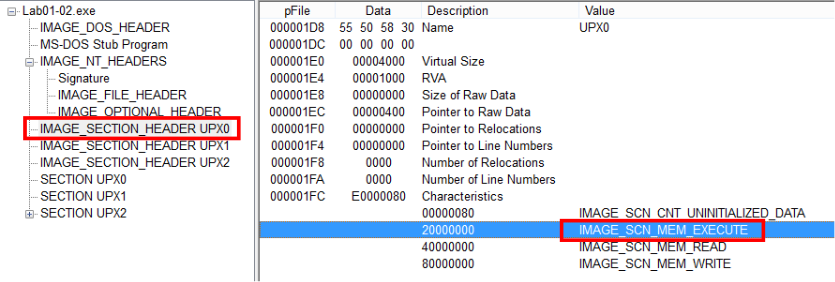
The UPX0 section, the largest one, is flagged as executable: the original unpacked code probably belongs to here. Executable sections have the IMAGE_SCN_MEM_EXECUTE characteristic set. The following screenshots show that characteristic - the first screenshot taken from within PEview, the second from within ExeinfoPE:
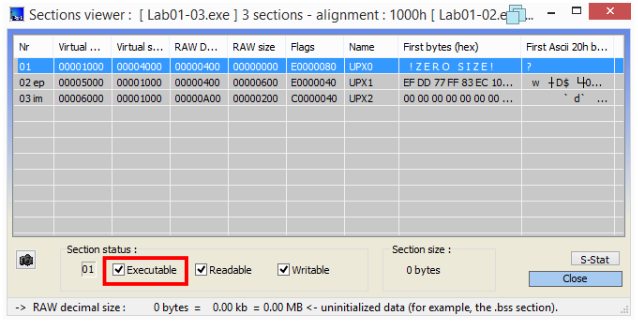
An examination of the strings contained in the executable also shows signs of packing: there are references to UPX and there seem to be only a few imports.
C:\malwarelab> strings2 -nh Lab01-02.exe
!This program cannot be run in DOS mode.
$
Rich
UPX0
UPX1
UPX2
3.04
a\`Y
|k
(23h
MalService
sHGL345
http://w
warean
ysisbook.co
om#Int6net Explo!r 8FEI
SystemTimeToFile
GetMo
*Waitab'r
Process
OpenMu$x
ZSB+
ForS
ObjectU4
Th
[Vrtb
CtrlDisp ch
Xcpt
mArg
5nm@_
t_fd
dlI37n
olfp
dW|6
lB`.rd
XPTPSW
KERNEL32.DLL
ADVAPI32.dll
MSVCRT.dll
WININET.dll
LoadLibraryA
GetProcAddress
VirtualProtect
VirtualAlloc
VirtualFree
ExitProcess
CreateServiceA
exit
InternetOpenA
Let’s try to unpack the sample with UPX:
C:\malwarelab> upx -d Lab01-02.exe -o Lab01-02.exe.unpacked
Opening the new executable with PEiD doesn’t show any indication of packing anymore:
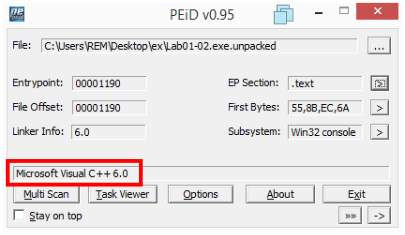
I can now get the correct sections information:
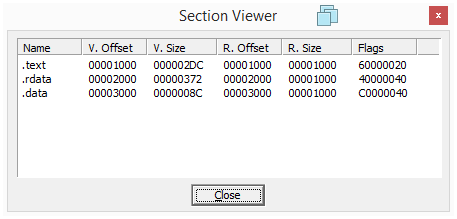
| Section | Virtual Size | Raw Size |
|---|---|---|
| .text | 2Dc | 1000 |
| .rdata | 372 | 1000 |
| .data | 8C | 1000 |
The unpacked executable now contains much more meaningful strings:
C:\malwarelab> strings2 -nh Lab01-02.exe.unpacked
!This program cannot be run in DOS mode.
$
Rich
.text
`.rdata
@.data
h(0@
Vh(0@
@jjjj
L$,j
@jjj
@jjj
=0 @
hT0@
=p @
h00@
SVW
|0@
x0@
=l0@
5p0@
%< @
%L @
%d @
%h @
KERNEL32.DLL
ADVAPI32.dll
MSVCRT.dll
WININET.dll
SystemTimeToFileTime
GetModuleFileNameA
CreateWaitableTimerA
ExitProcess
OpenMutexA
SetWaitableTimer
WaitForSingleObject
CreateMutexA
CreateThread
CreateServiceA
StartServiceCtrlDispatcherA
OpenSCManagerA
_exit
_XcptFilter
exit
__p___initenv
__getmainargs
_initterm
__setusermatherr
_adjust_fdiv
__p__commode
__p__fmode
__set_app_type
_except_handler3
_controlfp
InternetOpenUrlA
InternetOpenA
MalService
Malservice
HGL345
http://www.malwareanalysisbook.com
Internet Explorer 8.0
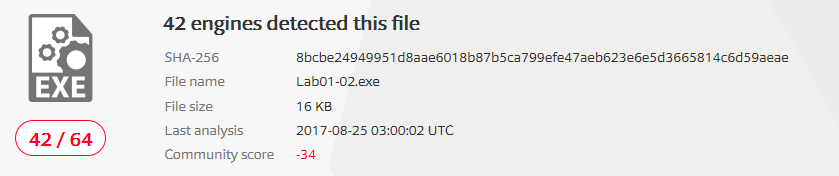
These are the hashes of the unpacked executable:
| MD5 | ae4ca70697df5506bc610172cfc288e7 |
| SHA1 | 31e8a82e497058ff14049cf283b337ec51504819 |
| SHA256 | 8bcbe24949951d8aae6018b87b5ca799efe47aeb623e6e5d3665814c6d59aeae |
I used the hashes to perform a search on VirusTotal. The unpacked sample is reported as malicious:
3) Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
These are the imports as shown within IDA Pro:
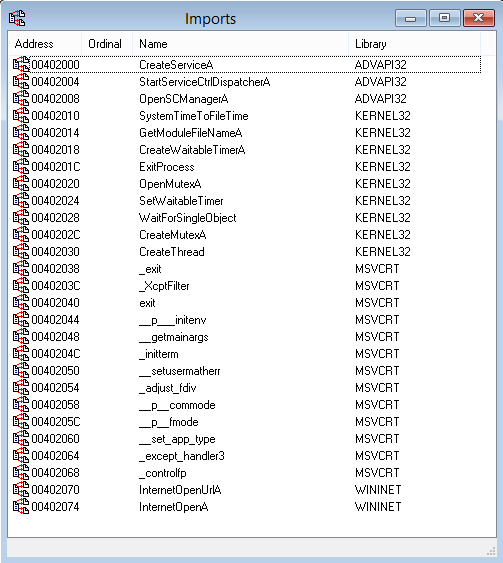
The sample Lab01-02.exe imports the following functions from ADVAPI32.dll:
CreateService
OpenSCManager
StartServiceCtrlDispatcher
This is an indication that the malware tries to install a service, a common persistence mechanism. Examining the strings included in the sample we can spot a suspicious Malservice which seems to be a plausible service name. I get a confirmation of this by checking with IDA:
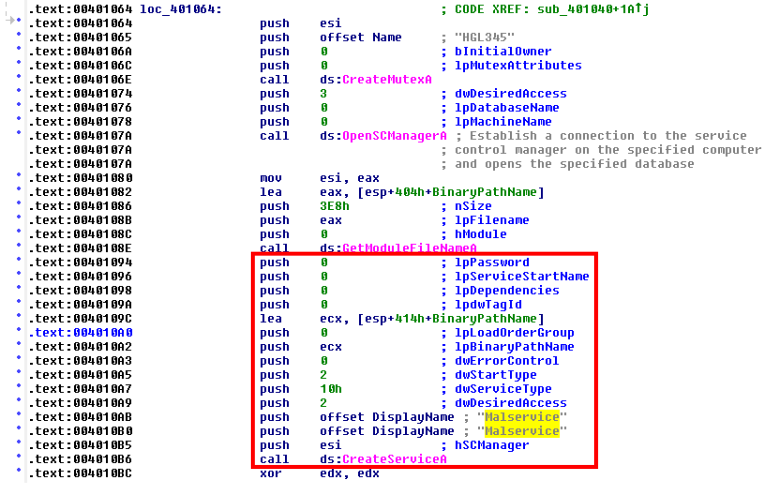
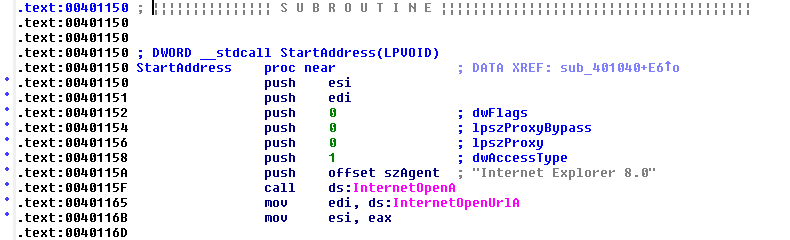
The malware also imports two interesting functions from WININET.dll, a library for performing high-level networking functions: InternetOpen and InternetOpenUrl. The string http://www.malwareanalysisbook.com is a significant clue that the sample is trying to open that URL using those functions. A quick check with IDA confirms this hypothesis and also reveals that the malware is connecting to that URL using the User-Agent Internet Explorer 8.0; this information is useful to detail a network-based indicator.
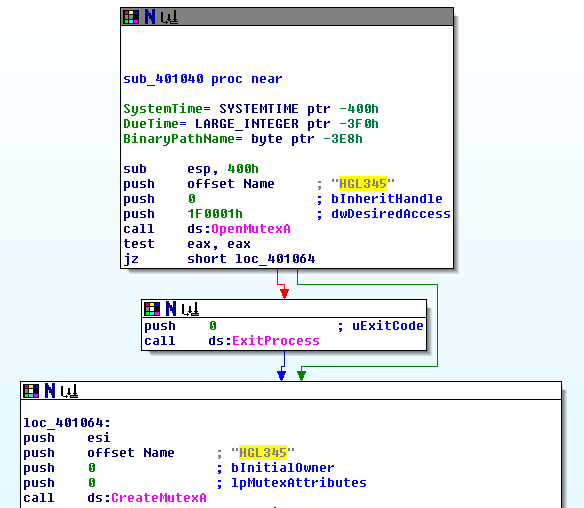
Lastly, the functions OpenMutex and CreateMutex imported from KERNEL32.dll let me think that this sample is checking if a mutex exists - a mutex is often used as an infection mark. The string HGL345 sounds like a good name for a mutex, and IDA confirms this idea:
5) What host- or network-based indicators could be used to identify this malware on infected machines?
On the basis of the analysis so far, these are the host- and network-based indicators that could be used to identify this malware:
- Service:
Malservice - Mutex:
HGL345 - URL:
http://www.malwareanalysisbook.comwith User-Agent:Internet Explorer 8.0
That’s all for this lab!