Practical Malware Analysis, Lab 1-3
This is a walkthrough of the Lab 1-3 from the book Practical Malware Analysis. The sample under analysis, Lab01-03.exe, has been packed in such a way that it cannot be easily unpacked just with basic static analysis techniques.
Please note that there may be many different (and even better) ways to solve this lab, so the one described here is just my solution.
The samples for this lab can be downloaded from here.
Let’s start!
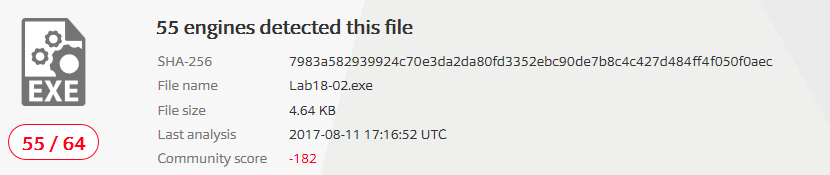
1) Upload the Lab01-03.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
I will compute the hash first and then look for that hash on VirusTotal.
| MD5 | 9c5c27494c28ed0b14853b346b113145 |
| SHA1 | 290ab6f431f46547db2628c494ce615d6061ceb8 |
| SHA256 | 7983a582939924c70e3da2da80fd3352ebc90de7b8c4c427d484ff4f050f0aec |
The VirusTotal report is available at the following links:
At present date the file is identified as malicious:
2) Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
Looking at the strings contained in the executable shows very few meaningful names:
C:\malwarelab> strings2 -nh Lab01-03.exe
!Windows Program
$PE
`.rdata
@.data
KERNEL32.dll
LoadLibraryA
GetProcAddress
":Ll
3Bt>O
VQ(8
2]<,M
P@M^
S>VW
AQ=h
I*G9>
e%nN
ole32.vd
Init
FoCr
U!!C
}OLEAUTLA
IMSVCRTT"b
_getmas
yrcs
|P2r3Us
p|vuy
fmod
4p
xF*l
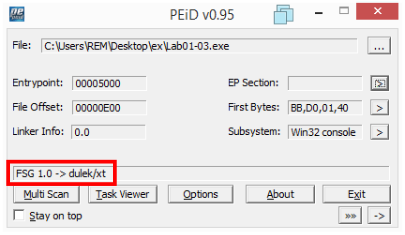
Opening the file with PEiD we can see that it’s been packed:
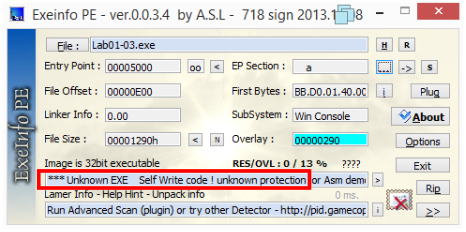
This is how it looks like in ExeinfoPE:
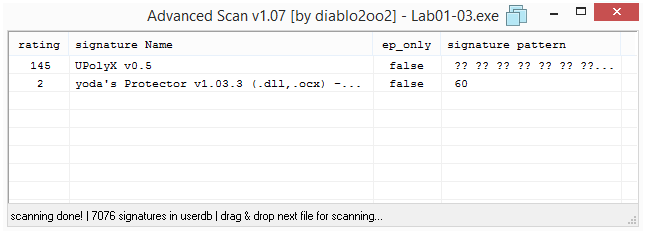
Running the Advanced Scan plugin from within ExeinfoPE gives additional hints about some unknown packer used:
Looking at the PE sections confirms that the executable has been packed:
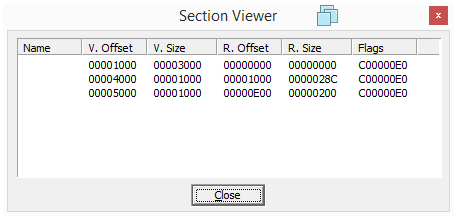
| Section | Virtual Size | Raw Size |
|---|---|---|
| 3000 | 0 | |
| 1000 | 28C | |
| 1000 | 200 |
Sections names are corrupted. Sections sizes in memory and on disk have suspicious values: the first section has a size of 0 bytes on disk but its size in memory is 0x3000 bytes: this is a strong indication of packing.
Trying to unpack the sample with UPX simply fails:
C:\malwarelab> upx -d Lab01-03.exe -o Lab01-03.exe.unpacked
upx: C:\malwarelab\Lab01-03.exe: NotPackedException: not packed by UPX
3) Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Looking at the strings we recognize only two imports: LoadLibrary and GetProcAddress.
This is the list of imports as showed from within Dependency Walker:
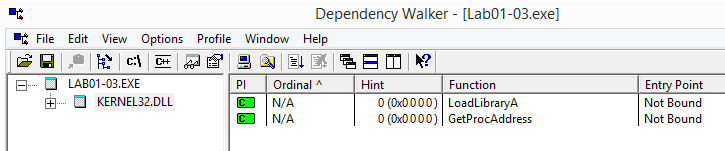
The imported functions LoadLibrary and GetProcAddress are two of the most commonly used functions: they let an executable load a DLL at runtime and then access any function from that DLL. When LoadLibrary and GetProcAddress are used we can’t tell just by static analysis which functions are going to be used by the malware since they won’t appear in the Import Address Table (IAT).
The only two imports are used to run the unpacking routines, so I can’t say anything else about the functionality of this malware withouth unpacking it first. To unpack this malware I will need to apply advanced static analysis techniques.
4) What host- or network-based indicators could be used to identify this malware on infected machines?
Can’t say.
That’s all for this lab, but I will get back to this sample later on in another post.