Practical Malware Analysis, Lab 3-1
This is a walkthrough of the Lab 3-1 from the book Practical Malware Analysis. The sample under analysis, Lab03-01.exe, performs some obscure network activity.
Please note that there may be many different (and even better) ways to solve this lab, so the one described here is just my solution.
The samples for this lab can be downloaded from here.
Let’s start!
Firstly I would compute the hashes and write them down for reference:
| MD5 | d537acb8f56a1ce206bc35cf8ff959c0 |
| SHA1 | 0bb491f62b77df737801b9ab0fd14fa12d43d254 |
| SHA256 | eb84360ca4e33b8bb60df47ab5ce962501ef3420bc7aab90655fd507d2ffcedd |
1) What are this malware’s imports and strings?
This malware seems to have very few imports, indeed only one. The following is a screenshot of PEview showing the imported function ExitProcess from kernel32.dll.
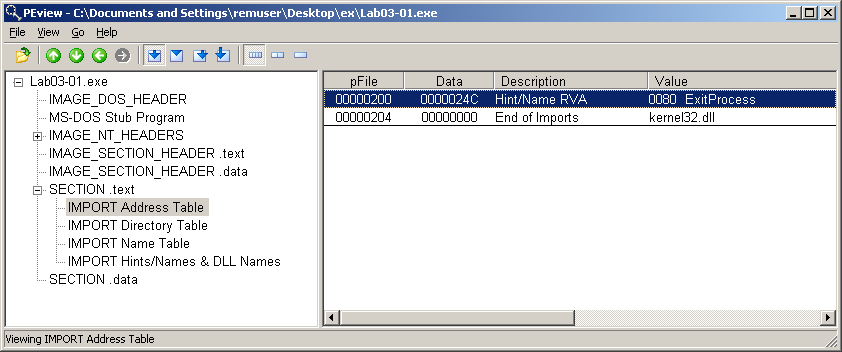
Having so few imports is a strong indication that the malware has been packed. We can get a confirmation of this by checking with PEiD:
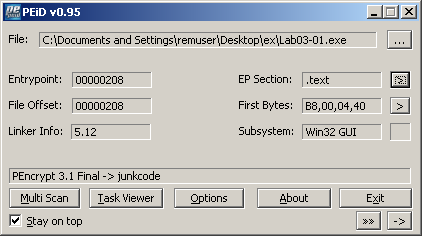
Examining the strings contained in the executable reveals some interesting clues regarding what the malware does. There are signs that it connects to the Internet: see the URL www.practicalmalwareanalysis.com. There are the names of some registry keys, like SOFTWARE\Microsoft\Windows\CurrentVersion\Run which is probably used as a persistence mechanism. The string vmx32to64.exe appears to be the name of a file.
This is an excerpt of the output obtained with the strings2 utility:
ExitProcess
kernel32.dll
ws2_32
CONNECT %s:%i HTTP/1.0
advapi32
ntdll
user32
advpack
StubPath
SOFTWARE\Classes\http\shell\open\command
Software\Microsoft\Active Setup\Installed Components\
test
www.practicalmalwareanalysis.com
admin
VideoDriver
WinVMX32
vmx32to64.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
AppData
2) What are the malware’s host-based indicators?
Let’s perform some basic dynamic analysis to find out what the malware does.
I’m going to use two virtual machines: one is the Windows XP Lab workstation where I will detonate the malware; the other is the REMnux Lab workstation which I will use to direct the network traffic to.
To monitor network activity:
-
I would set up ApateDNS on the Windows XP box to intercept any DNS requests and have it reply with the IP address of the REMnux box.
-
On the REMnux box I would set up INETsim to simulate Internet services, and Wireshark to sniff network traffic.
-
I’m going to monitor network traffic with Wireshark on the Windows XP box as well.
To monitor system activity on the Windows box I would run:
I would let them run, and exclude normal activity from Process Monitor. Then, right before detonating the malware, I would take the first shot with Regshot.
I would detonate the sample Lab03-01.exe. By observing it running in Process Explorer, I can reveal the name of a mutex in the process handles, as shown in the picture:
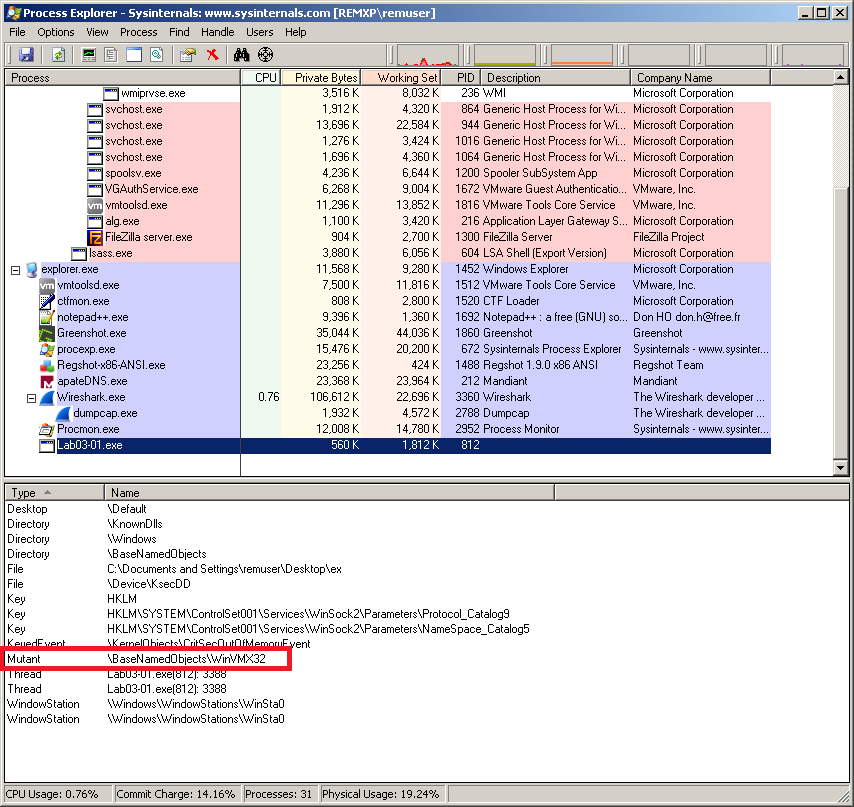
The mutex WinVMX32 is a host-based indicator.
A couple of minutes after detonation, I would take the second shot with Regshot, and then stop capturing with Process Monitor and Wireshark.
By comparing the two shots taken, I see that the malware created the file C:\WINDOWS\system32\vmx32to64.exe which is a copy of the malware itself (its hash matches the original sample).
The malware also wrote the following key to the registry: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\VideoDriver with value C:\WINDOWS\system32\vmx32to64.exe. This is clearly used as a persistence mechanism.
The file and the registry key/value are also good host-based indicators.
The activity performed by the malware on the system can be also seen by analyzing the log of Process Monitor. I would set it to filter Lab03-01.exe process and WriteFile or RegSetValue operations. This is what I get:
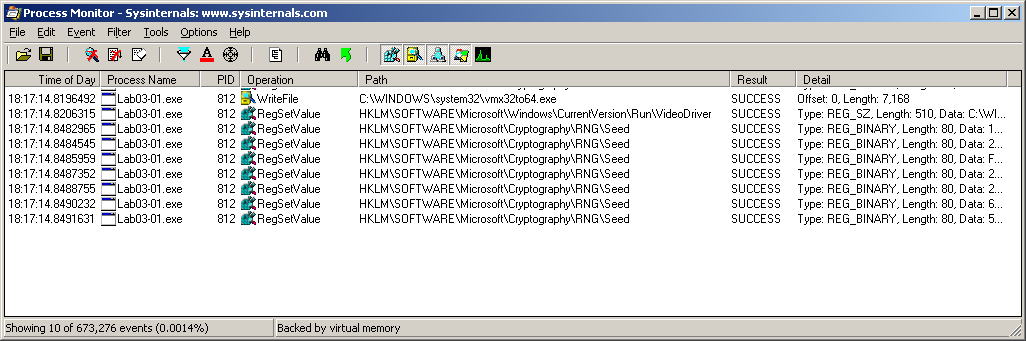
The registry key HKLM\SOFTWARE\Microsoft\Cryptography\RNG\Seed refers to the random number generator seed, and is not of much interest since it is always being updated in the registry by software.
3) Are there any useful network-based signatures for this malware? If so, what are they?
Network activity can be observed in the logs of ApateDNS, INETsim and of course Wireshark.
The malware tries to contact www.practicalmalwareanalysis.com on port 443, and it does so every 30 seconds. Packets are consistent in size (256 bytes) and contains apparently random data:
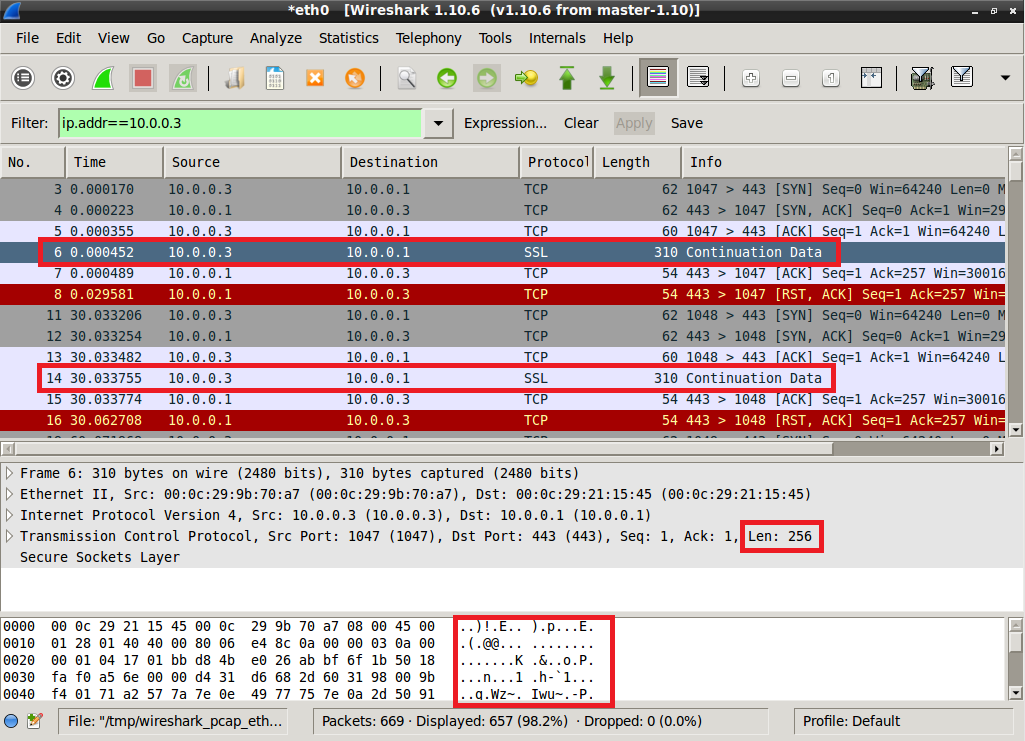
Packets payload data is not related to SSL/TLS protocol: the handshake fails, as apparent from the INETsim log:
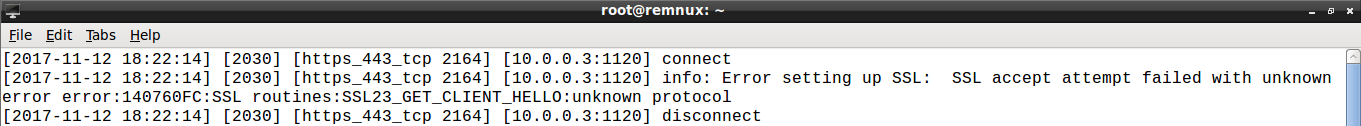
Performing again the analysis a couple of times let me observe the same behaviour.
That’s all for this lab!