Practical Malware Analysis, Lab 3-2
This is a walkthrough of the Lab 3-2 from the book Practical Malware Analysis. The sample under analysis, Lab03-02.dll, is a malware that must be installed as a service.
Please note that there may be many different (and even better) ways to solve this lab, so the one described here is just my solution.
The samples for this lab can be downloaded from here.
Let’s start!
Before answering the questions on this Lab, I will perform some basic static analysis. The results will be useful to answer the questions.
I would compute the hashes and write them down for reference:
| MD5 | 84882c9d43e23d63b82004fae74ebb61 |
| SHA1 | c6fb3b50d946bec6f391aefa4e54478cf8607211 |
| SHA256 | 5eced7367ed63354b4ed5c556e2363514293f614c2c2eb187273381b2ef5f0f9 |
The sample is a DLL. I can check with PEiD that it’s not packed; good indications of not being packed are also:
- its PE sections look normal: no strange names,coherent virtual and raw sizes;
- there are many imports, as apparent from a quick analysis with PEview or DependencyWalker;
- it contains many meaningful strings.
On the basis of a quick analysis of its strings, I can deduce the following:
Network activity
The malware performs some network activity: there is indication of a host practicalmalwareanalysis.com which may get contacted over HTTP/1.1 maybe to request the file serve.html.
Base64 encoding
The following string is the Base64 alphabet; this is a hint that the malware performs base64 encoding/decoding. ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/
Indeed I can find these strings to be base64-encoded:
| Base64-encoded string | Decoded value |
|---|---|
Y29ubmVjdA== |
connect |
dW5zdXBwb3J0 |
unsupport |
c2xlZXA= |
sleep |
Y21k |
cmd |
cXVpdA== |
quit |
Those strings may be commands that the malware is able receive and execute. The strings exit and getfile too look interesting.
Service as persistence mechanism
The malware creates a Windows service as suggested by these imported functions:
RegisterServiceCtrlHandlerA
CloseServiceHandle
CreateServiceA
OpenSCManagerA
DeleteService
OpenServiceA
SetServiceStatus
By searching the label CreateServiceA in IDA Pro (press Ctrl+L and double click on the label you’re searching for, and then press Ctrl+X to jump to the address where the function is called from), I can get information on the display name of the service: Intranet Network Awareness (INA+).
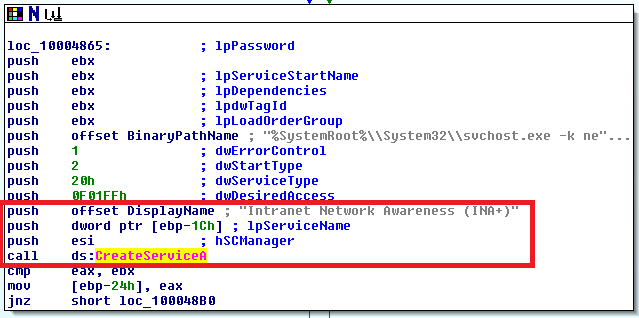
Scrolling the code backward, we get to the beginning of the Install routine, where we can read the name of service: IPRIP.
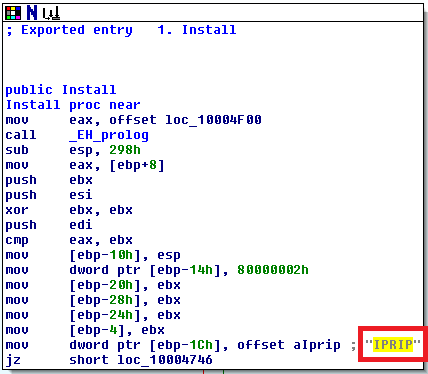
So I will be expecting the malware to create a service named IPRIP and with display name Intranet Network Awareness (INA+): behavioral analysis will confirm this.
Registry activity
The malware also performs operations on the registry as suggested by these imports and registry keys names:
RegSetValueExA
RegCreateKeyA
RegCloseKey
RegQueryValueExA
RegOpenKeyExA
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost
SYSTEM\CurrentControlSet\Services\
Exported functions
Since this sample is a DLL, it’s worth taking a look at its exported functions. The exports contain a function named installA:
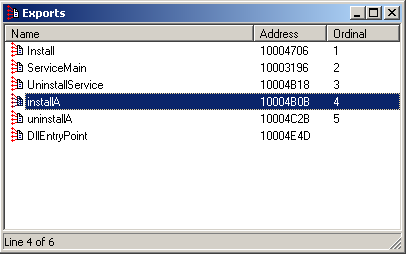
It looks like installA is the function to call to make the malware install itself; this function in turn will call the function Install.
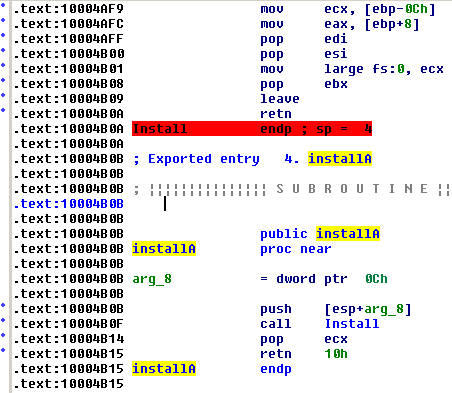
So on the basis of this initial analysis let’s now answer the Lab questions.
1) How can you get this malware to install itself?
I can get to install the malware manually by invoking the following command:
rundll32.exe Lab03-02.dll, installA
Before executing this command, I would set up network and system monitoring. I’m going to use two virtual machines: one is the Windows XP Lab workstation where I will detonate the malware; the other is the REMnux Lab workstation which I will use to direct the network traffic to.
To monitor network activity:
- I would set up ApateDNS on the Windows XP box to intercept any DNS requests and have it reply with the IP address of the REMnux box.
- On the REMnux box I would set up INETsim to simulate Internet services, and Wireshark to sniff network traffic.
- I’m going to monitor network traffic with Wireshark on the Windows XP box as well.
To monitor system activity on the Windows box I would run:
I would let those programs run, and exclude normal activity from Process Monitor. Then, right before installing the malware, I would take the first shot with Regshot.
Now I can install the malware.
I can check that a new service has been created with name IPRIP and display name Intranet Network Awareness (INA+), as expected.
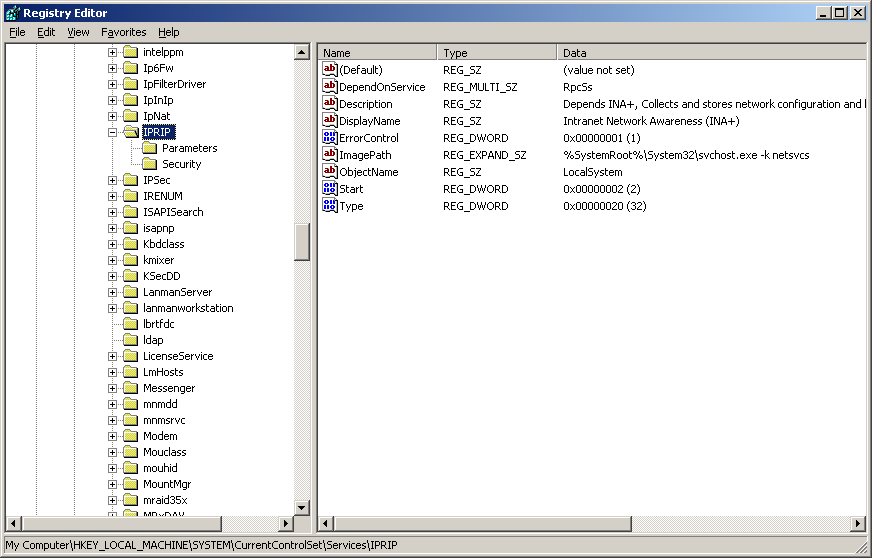
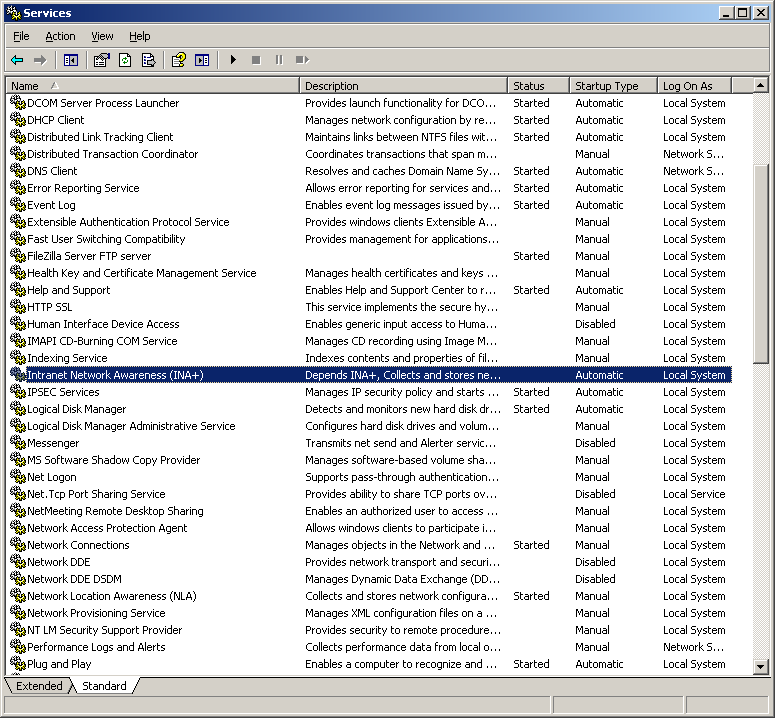
2) How would you get this malware to run after installation?
The new service is set to start automatically on Windows startup; I can make it start right away manually.
Before doing that, let’s check what’s happened so far, taking the second shot with Regshot and comparing the two shots. I see that new keys and values have been added to the registry for the service definition.
HKLM\SYSTEM\ControlSet001\Services\IPRIP\{...}
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\{...}
One of the key/value created by the malware is:
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\ImagePath: "%SystemRoot%\System32\svchost.exe -k netsvcs"
Being a DLL this malware depends on an executable to start. Indeed the image path of the service is svchost.exe; that means the malware will be running under this process.
To run the malware I will start the service:
net start IPRIP
Looking in Process Explorer I will find which svchost service the malware is hiding in: hovering the mouse over each svchost process and checking the associated services will reveal the malicious one. The services registered in a process can be showed also in the Services tab of the process properties window.
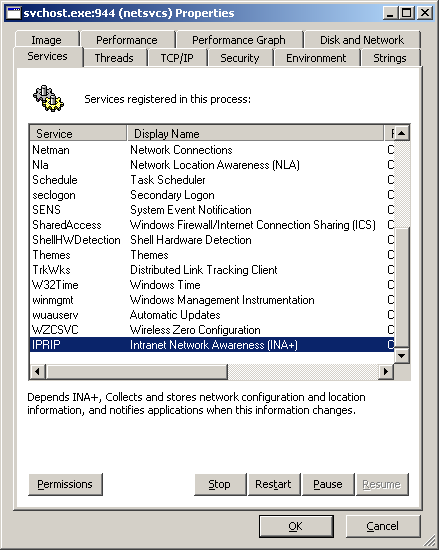
In Process Explorer we can also search for a specific DLL loaded by a process by selecting Find and Find Handle or DLL and typing the name Lab03-02.dll; it will reveal that the process svchost with PID 944 is the one I was looking for.
3) Which filters could you set in order to use procmon to glean information?
I can use the PID of the process which I found with Process Explorer to make a filter in ProcMon.
4) What are the malware’s host-based indicators?
The malware installs itself as a service named IPRIP and with display name Intranet Network Awareness (INA+). It creates these key in the Windows registry for persistence:
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\
5) Are there any useful network-based signatures for this malware?
After running the malware, it waits 60 seconds before performing any network activity.
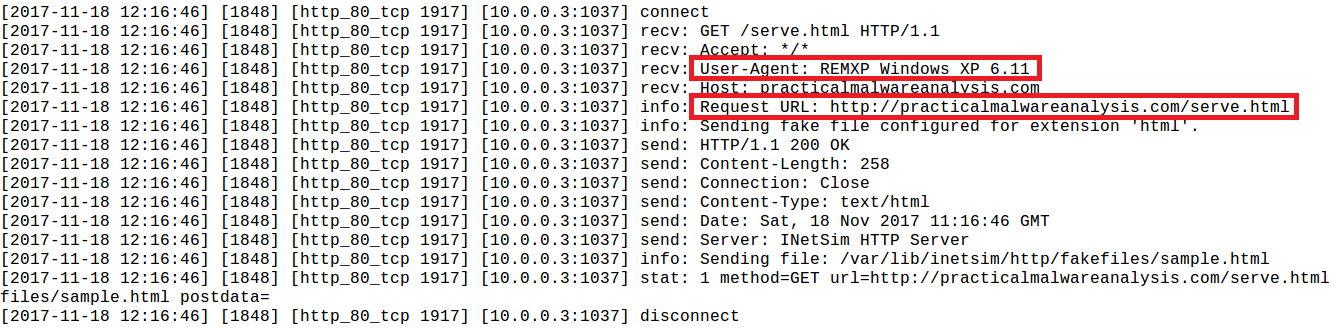
The malware tries to contact the host practicalmalwareanalysis.com as evident in the log of ApateDNS:
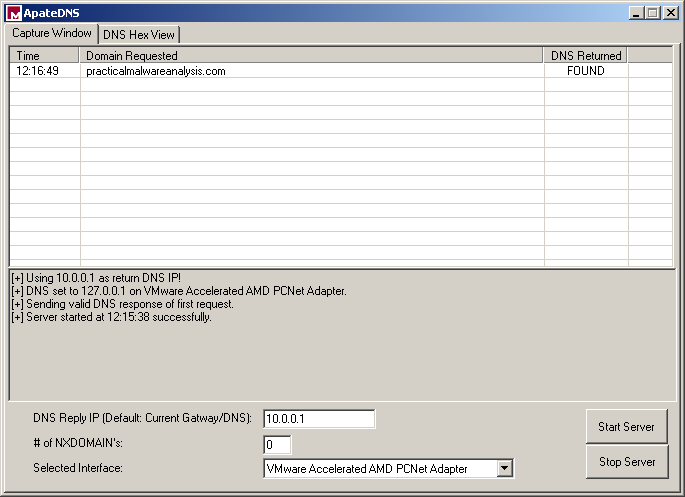
It sends HTTP traffic to that host, using REMXP Windows XP 6.11 as the User-Agent (the first part of the string is the machine name, REMXP in my case).
That’s all for this lab!