Practical Malware Analysis, Lab 3-3
This is a walkthrough of the Lab 3-3 from the book Practical Malware Analysis. The sample under analysis, Lab03-03.exe, is hiding itself as another process.
Please note that there may be many different (and even better) ways to solve this lab, so the one described here is just my solution.
The samples for this lab can be downloaded from here.
Let’s start!
Let me first compute the hashes and write them down for reference:
| MD5 | e2bf42217a67e46433da8b6f4507219e |
| SHA1 | daf263702f11dc0430d30f9bf443e7885cf91fcb |
| SHA256 | ae8a1c7eb64c42ea2a04f97523ebf0844c27029eb040d910048b680f884b9dce |
I’m going to perform basic dynamic analysis. Before executing the malware, I would set up network and system monitoring. I’m going to use two virtual machines: one is the Windows XP Lab workstation where I will detonate the malware; the other is the REMnux Lab workstation which I will use to direct the network traffic to.
To monitor network activity:
- I would set up ApateDNS on the Windows XP box to intercept any DNS requests and have it reply with the IP address of the REMnux box.
- On the REMnux box I would set up INETsim to simulate Internet services, and Wireshark to sniff network traffic.
- I’m going to monitor network traffic with Wireshark on the Windows XP box as well.
To monitor system activity on the Windows box I would run:
I would let those programs run, and exclude normal activity from Process Monitor. Then, right before installing the malware, I would take the first shot with Regshot.
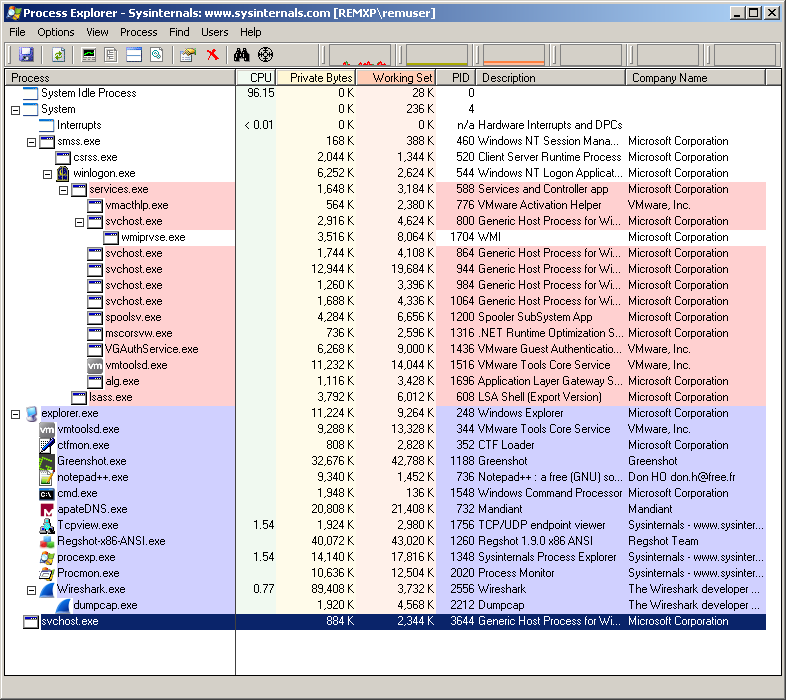
1) What do you notice when monitoring this malware with Process Explorer?
I see that the malware creates a process named scvhost.exe before exiting. The svchost.exe process keeps running as an orphaned process, i.e. it does not have any parent: this is suspicious indeed since svchost.exe is normally a child of services.exe.
2) Can you identify any live memory modifications?
If we look at the properties of this process (double-click the process in Process Explorer), the executable apparently looks normal. I can even try to Verify it (i.e. Process Explorer will check if the disk image signature matches the signature of the original Microsoft executable) and the result is positive: notice the (Verified) tag in the screenshot:
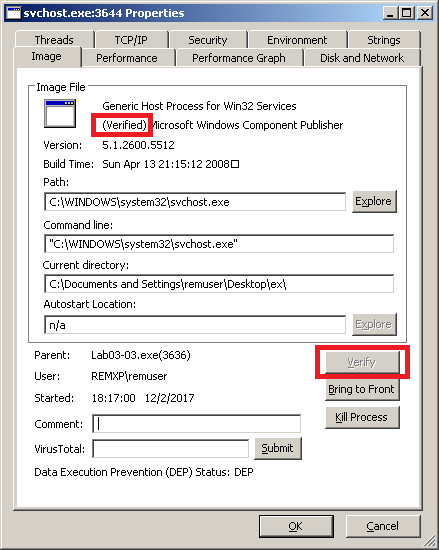
Nevertheless, I notice that the strings contained in the disk image differ from the strings in memory:
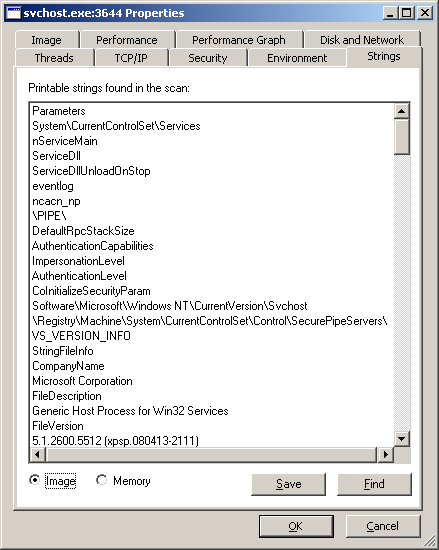
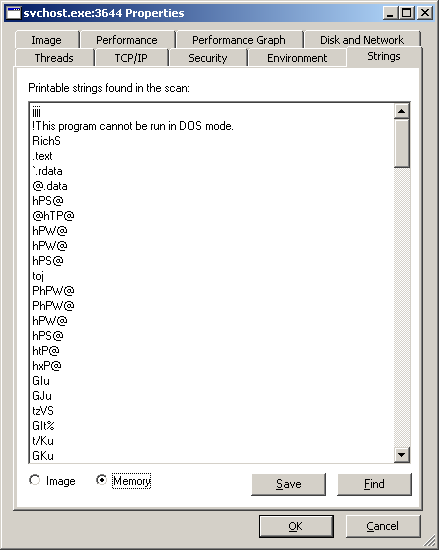
This does mean that the malware performed process replacement: it first spawned an authentic svchost.exe process, then it replaced its memory with malicious code.
The screenshot below shows the bottom of the list of strings in memory:
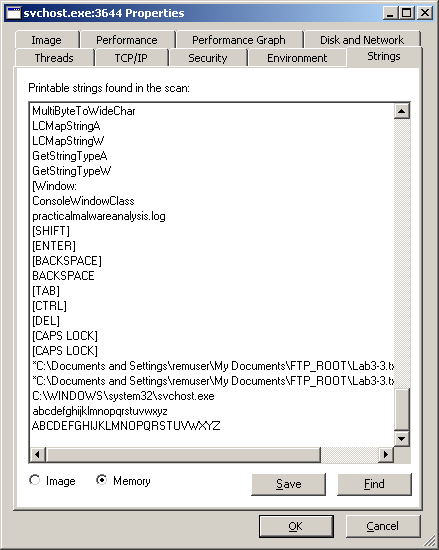
Some of the strings ([SHIFT], [ENTER], [BACKSPACE], [TAB], …) make me guess that this malware may be a keylogger. There is also the name of a file (practicalmalwareanalysis.log) that supports this hypothesis. Let’s go ahead with the analysis.
3) What are the malware’s host-based indicators?
Comparing the two shots taken with Regshot, I see that the malware writes a file to disk:
C:\Documents and Settings\remuser\Desktop\ex\practicalmalwareanalysis.log
This is a host-based indicator.
Setting a filter in Procmon to show only the process with the PID of svchost.exe (I get the PID from Process Explorer), I see that the malware writes to this file.
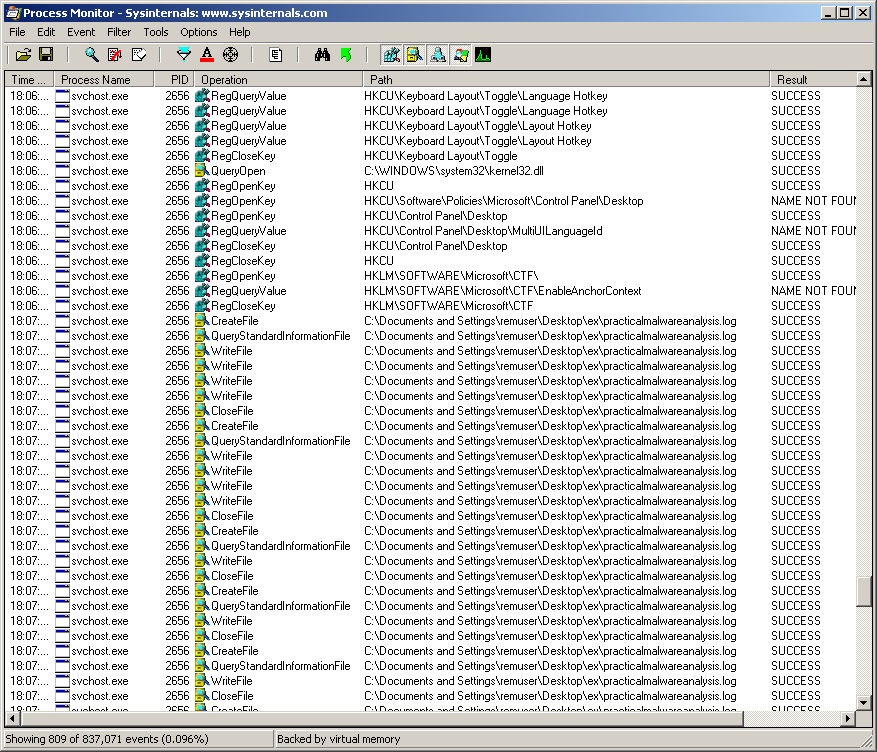
4) What is the purpose of this program?
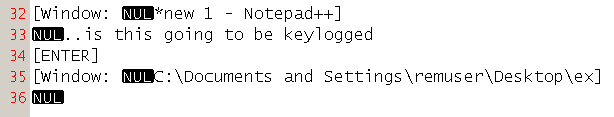
After opening the practicalmalwareanalysis.log file, I get confirmation that the malware replaced the memory of svchost.exe with malicious code performing keylogging functionality.
This is part of the content of the log file after I typed some words in notepad: it’s definitely a keylogger.
That’s all for this lab!